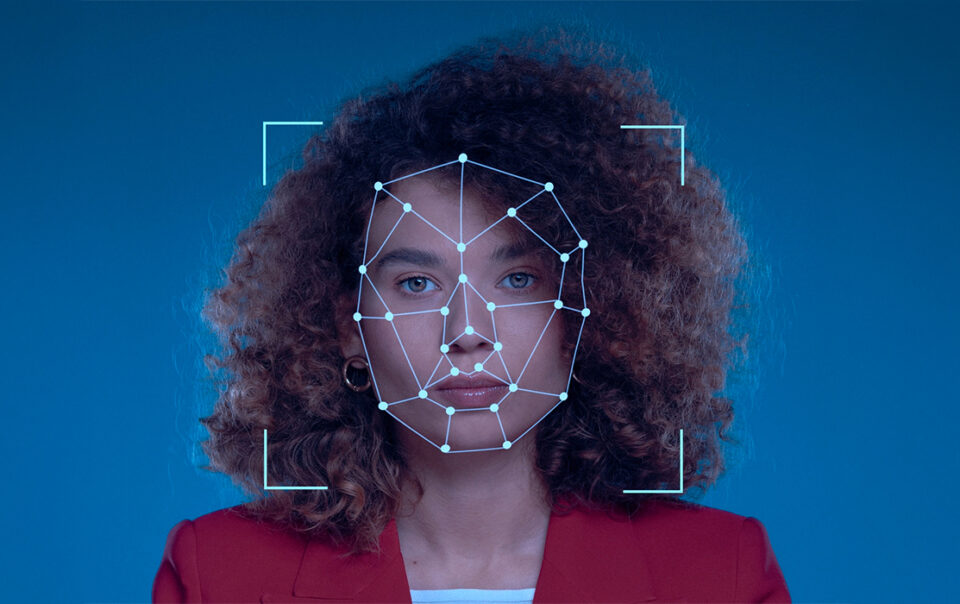
What is KYC? Ever wondered why banks and financial institutions make you go through a bunch of identity checks before opening an account? That’s Know Your Customer (KYC) in action. It’s a process businesses—especially in regulated industries—use to confirm their […]